Introduction to Endpoint Security
In today's digital landscape, cybersecurity threats are becoming increasingly sophisticated, making it essential for organizations to prioritize endpoint security. Endpoint security refers to the practice of protecting endpoint devices such as laptops, desktops, mobile devices, and servers from cyber threats. These devices are the entry points for most cyber attacks, and if not properly secured, can provide an open door for hackers to gain access to an organization's network and sensitive data. In this article, we will explore the importance of endpoint security, the types of threats that endpoints face, and the best practices for protecting the perimeter of an organization's network.
Understanding Endpoint Threats
Endpoint threats can come in many forms, including malware, ransomware, phishing attacks, and unauthorized access. Malware, short for malicious software, is designed to harm or exploit a computer system. Ransomware is a type of malware that encrypts a victim's files and demands a ransom in exchange for the decryption key. Phishing attacks involve tricking users into revealing sensitive information such as passwords or credit card numbers. Unauthorized access occurs when an individual gains access to a device or network without permission. These threats can have devastating consequences, including data breaches, financial loss, and damage to an organization's reputation.
For example, in 2017, the WannaCry ransomware attack affected over 200,000 computers in 150 countries, causing widespread disruption and financial loss. The attack highlighted the importance of keeping endpoint devices up to date with the latest security patches and software updates. In another example, the 2019 Capital One data breach, which exposed the sensitive information of over 100 million customers, was caused by a misconfigured web application firewall, demonstrating the need for robust security measures to protect endpoints.
Best Practices for Endpoint Security
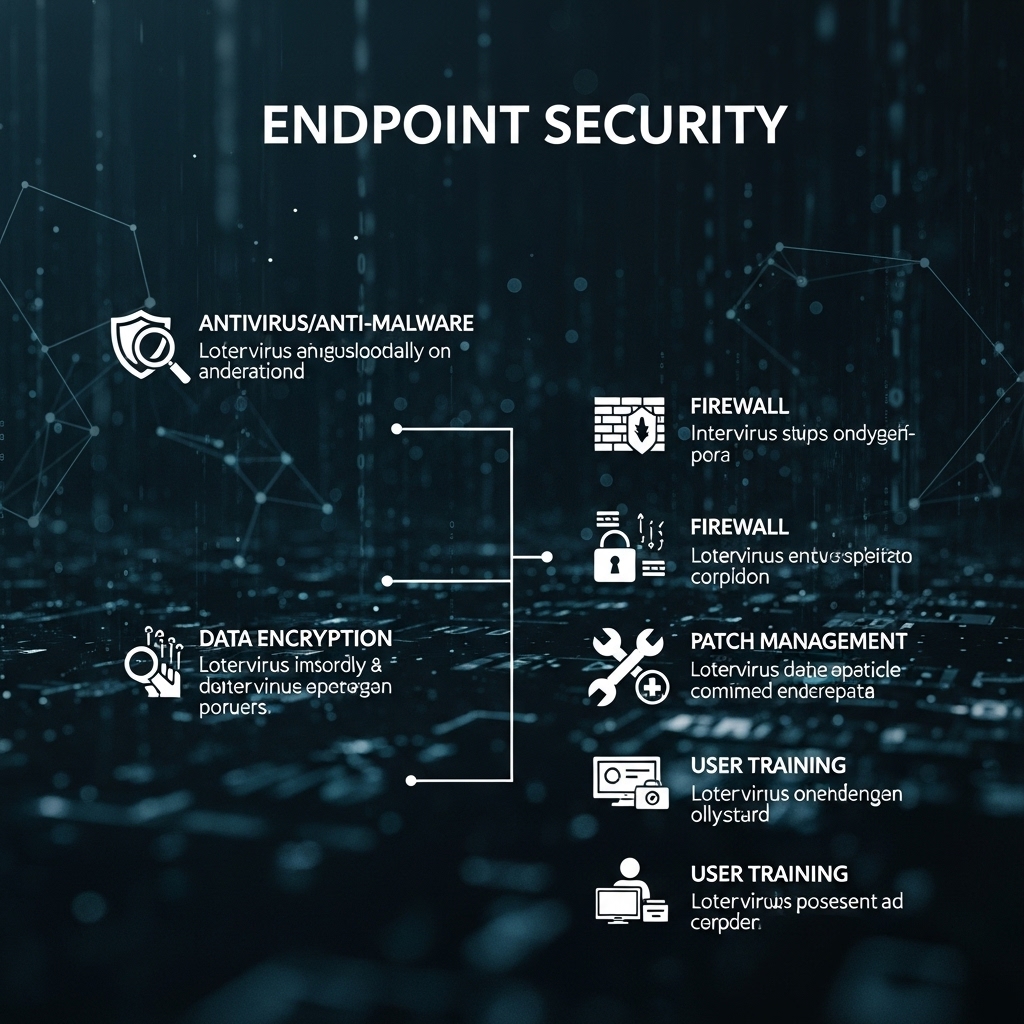
To protect endpoints from cyber threats, organizations should implement a range of security measures. First, all endpoint devices should be equipped with up-to-date antivirus software and a firewall. Antivirus software can detect and remove malware, while a firewall can block unauthorized access to a device or network. Additionally, organizations should implement a patch management program to ensure that all endpoint devices have the latest security patches and software updates. This can help to prevent exploitation of known vulnerabilities.
Another best practice is to use strong authentication and authorization measures, such as multi-factor authentication, to prevent unauthorized access to endpoint devices. Multi-factor authentication requires users to provide multiple forms of verification, such as a password and a fingerprint, to access a device or network. Organizations should also implement a least privilege access model, which restricts user access to only the resources and data necessary to perform their job functions.
Endpoint Detection and Response
Endpoint detection and response (EDR) is a critical component of endpoint security. EDR involves monitoring endpoint devices for suspicious activity and responding quickly to potential threats. This can be achieved through the use of EDR software, which can detect and respond to threats in real-time. EDR software can also provide visibility into endpoint activity, allowing security teams to identify and respond to potential threats before they cause harm.
For example, an EDR system may detect a suspicious process running on an endpoint device and automatically block it, preventing a potential attack. The system may also alert security teams to investigate and respond to the potential threat. In addition, EDR software can provide forensic analysis capabilities, allowing security teams to investigate and analyze the root cause of a security incident.
Cloud-Based Endpoint Security
Cloud-based endpoint security is becoming increasingly popular, as it provides a range of benefits, including scalability, flexibility, and cost-effectiveness. Cloud-based endpoint security solutions can be easily deployed and managed, and can provide real-time threat protection and detection. These solutions can also provide advanced analytics and reporting capabilities, allowing security teams to gain visibility into endpoint activity and make informed security decisions.
For example, a cloud-based endpoint security solution may use machine learning algorithms to detect and respond to threats in real-time. The solution may also provide a cloud-based console, allowing security teams to manage and monitor endpoint devices from a single location. In addition, cloud-based endpoint security solutions can provide integration with other security tools and systems, such as SIEM and SOAR solutions.
Implementing a Zero Trust Model
A zero trust model is a security approach that assumes that all users and devices are untrusted, and verifies their identity and permissions before granting access to resources and data. This approach can help to prevent lateral movement and reduce the risk of a security breach. To implement a zero trust model, organizations should start by identifying and classifying sensitive data and resources, and then implement access controls and authentication measures to restrict access to these resources.
For example, an organization may implement a zero trust model by requiring all users to authenticate using multi-factor authentication, and then granting access to resources and data based on user identity and permissions. The organization may also implement micro-segmentation, which involves dividing a network into smaller segments and restricting access to each segment based on user identity and permissions.
Conclusion
In conclusion, protecting the perimeter of an organization's network is critical in today's digital landscape. Endpoint security is a critical component of this effort, and involves protecting endpoint devices from cyber threats. By implementing best practices, such as keeping endpoint devices up to date with the latest security patches and software updates, using strong authentication and authorization measures, and implementing EDR and cloud-based endpoint security solutions, organizations can reduce the risk of a security breach and protect sensitive data. Additionally, implementing a zero trust model can help to prevent lateral movement and reduce the risk of a security breach. By prioritizing endpoint security, organizations can help to ensure the security and integrity of their network and data.
