MCQ Question: How does the Transmission Control Protocol (TCP) ensure reliable data transmission over the Internet?
- A. By sending packets without checking delivery status to maximize speed
- B. By implementing connectionless communication similar to UDP
- C. Through acknowledgements, retransmissions, congestion control, and ordered delivery guarantees
- D. By encrypting all packets end-to-end by default
Correct Answer: C
Explanation (extended — approx. 1000 words):
TCP (Transmission Control Protocol) is one of the most important protocols in the Internet Protocol Suite. It operates at the transport layer of the OSI model and plays the central role of ensuring reliable, ordered, and error-checked delivery of data between applications communicating over IP networks. Unlike UDP, which is connectionless and provides no delivery guarantees, TCP is connection-oriented and carefully manages every stage of communication — from establishing a connection, to transferring data segments, to gracefully closing the connection. This reliability is achieved through a set of integrated mechanisms: acknowledgements (ACKs), retransmissions, sequence numbers, flow control, congestion control, and ordered delivery. Together, these mechanisms allow TCP to function robustly even on networks that experience packet loss, delay, duplication, or reordering.
1. Connection establishment (Three-Way Handshake)
Before data transfer begins, TCP establishes a logical connection between a client and server. This is done using the famous three-way handshake: SYN → SYN-ACK → ACK. During this process, both parties exchange initial sequence numbers which will serve as identifiers for tracking each byte of the data stream. This handshake sets up the environment for reliable communication, confirming that both sides are ready and synchronized.
2. Sequence numbers and ordered delivery
TCP assigns a unique sequence number to every byte of data transmitted. These sequence numbers allow the receiving side to reassemble the stream in the correct order even when packets arrive out of sequence. On the Internet, packet reordering is common due to dynamic routing, parallel paths, and load balancing. TCP solves this by buffering out-of-order packets and delivering the reconstructed byte stream to the application only when all preceding bytes have arrived.
3. Acknowledgements and retransmissions
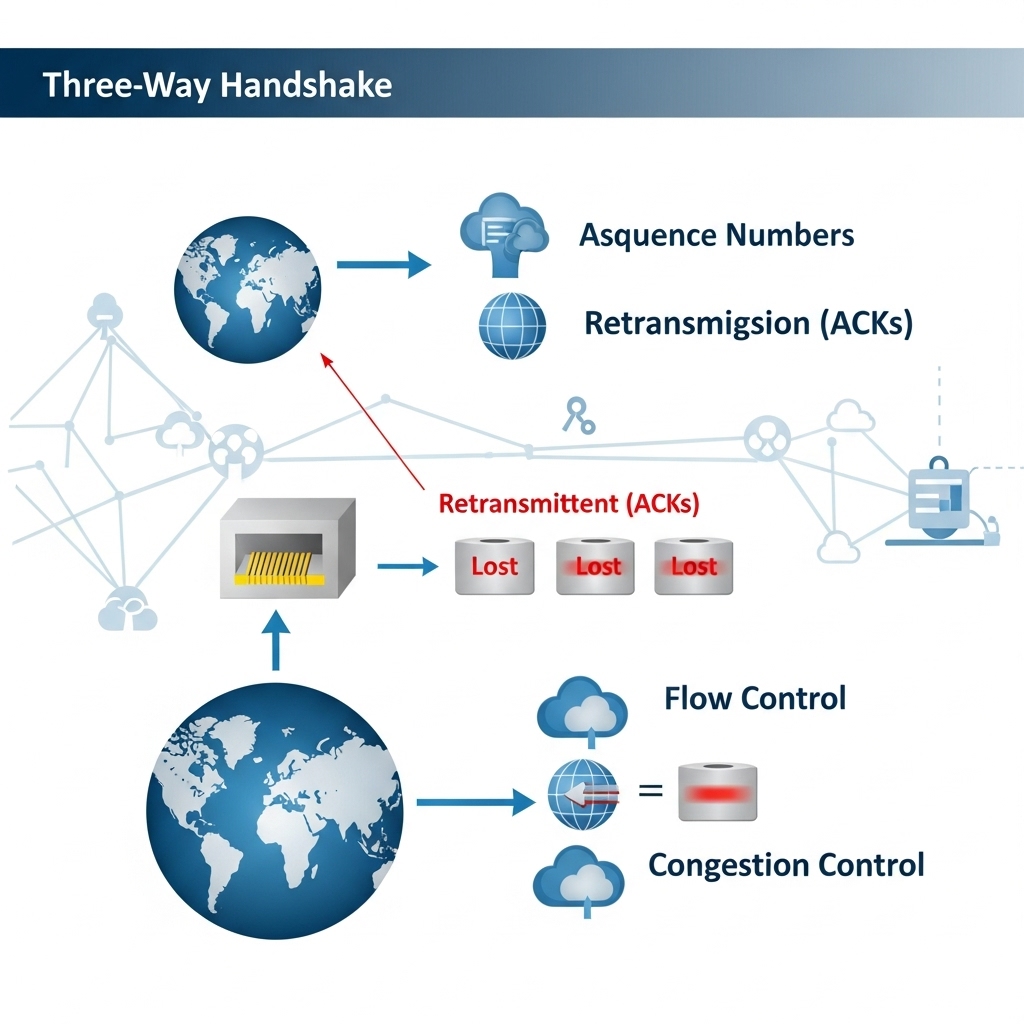
Reliability hinges on acknowledgements (ACKs). When a receiver successfully obtains data, it sends back an ACK specifying the next byte it expects. If a packet or segment is lost in transit (detected by missing ACKs or duplicate ACKs), TCP triggers retransmission. This ensures that corrupted, dropped, or delayed packets do not interrupt the communication. The combination of sequence numbers and acknowledgements allows TCP to guarantee that every byte arrives at its destination exactly once.
4. Flow control (Receiver-side regulation)
Flow control prevents the sender from overwhelming the receiver with more data than it can process or buffer. TCP uses a sliding window technique, in which the receiver continuously advertises a “window size” indicating how much additional data it can accept. If the receiver becomes overloaded, it reduces the window size, signaling the sender to slow down. This dynamic adjustment ensures stable performance even when the receiving side’s capacity changes in real time.
5. Congestion control (Network-side protection)
Congestion control is one of TCP’s most sophisticated mechanisms. The Internet is a shared, unpredictable environment where sudden spikes in traffic can cause congestion collapse if unmanaged. TCP continually analyzes network conditions using algorithms like Slow Start, Congestion Avoidance, Fast Retransmit, and Fast Recovery. When packet loss is detected — often interpreted as a sign of congestion — TCP reduces its sending rate. When the network appears healthy, TCP cautiously increases throughput. These adaptive behaviors ensure fair resource usage among many simultaneous connections and prevent catastrophic network overload.
6. Error detection using checksums
To ensure data integrity, TCP includes a checksum in every segment. The receiver verifies this checksum to detect corruption. If corruption is detected, the receiver simply drops the segment, relying on TCP's retransmission mechanism to restore the data. This layered approach further strengthens reliability.
7. Full-duplex communication
TCP supports full-duplex transmission, meaning data can flow in both directions simultaneously. Each direction maintains its own sequence numbers and ACKs. This structure enables complex interactive applications — such as SSH, HTTPS, chat systems, and APIs — to function smoothly and without delay or confusion.
8. Graceful connection termination
When communication is complete, TCP uses a four-way handshake (FIN → ACK → FIN → ACK) to ensure both sides have finished sending data and are ready to close the connection. This orderly shutdown prevents data truncation and ensures no residual bytes linger unacknowledged.
Real-world applications where TCP reliability is critical
- Web browsing (HTTP/HTTPS): Ensures pages, scripts, and resources arrive intact and ordered.
- Email (SMTP, IMAP, POP3): Requires guaranteed, complete message delivery.
- File transfer (FTP, SFTP): Relies on byte-accurate transmission to maintain file integrity.
- Databases over networks: Transactions must not lose or duplicate data.
- Remote access (SSH): Requires full reliability for secure command execution.
Why not always use TCP?
Because TCP’s reliability mechanisms introduce overhead. For applications where speed and low latency matter more than guaranteed delivery — such as gaming, live streaming, video conferencing — UDP is preferred. These applications can tolerate occasional packet loss but cannot tolerate retransmission delays.
Summary: TCP ensures reliable communication through a combination of sequencing, acknowledgements, retransmissions, flow control, congestion control, and orderly connection management. These mechanisms allow it to deliver a perfectly reconstructed byte stream despite the Internet’s inherently unreliable environment. Its sophistication makes it indispensable for most modern web, communication, and data applications.

Post a Comment