Introduction to Web Application Security Protocols
Web application security is a critical aspect of protecting online businesses and organizations from cyber threats. As more companies move their operations online, the importance of securing web applications has never been more pressing. Web application security protocols are designed to prevent unauthorized access, use, disclosure, disruption, modification, or destruction of computer systems, networks, and data. However, despite the best efforts of developers and security professionals, vulnerabilities in web application security protocols remain a significant concern. In this article, we will explore common vulnerabilities in web application security protocols and discuss ways to mitigate them.
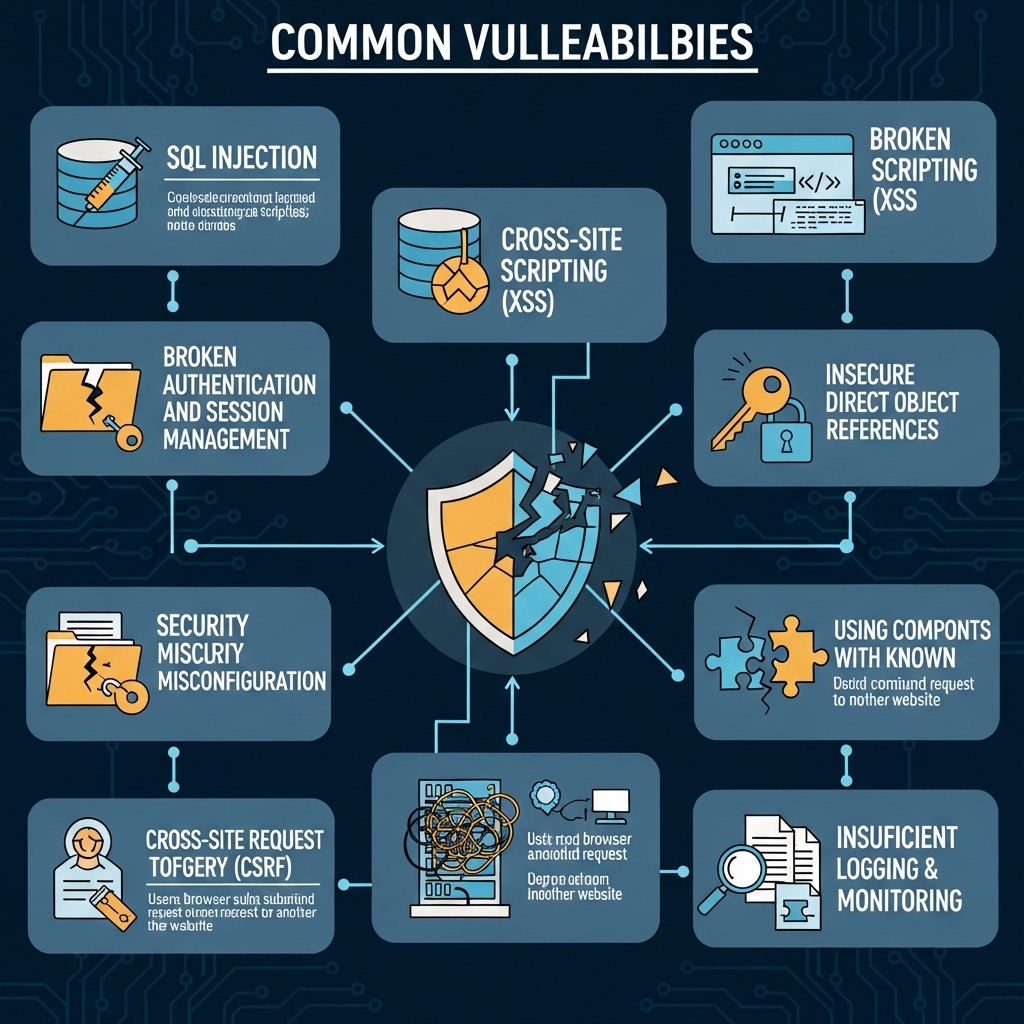
SQL Injection Vulnerabilities
SQL injection is a type of attack where an attacker injects malicious SQL code into a web application's database in order to extract or modify sensitive data. This type of attack is particularly dangerous because it can allow an attacker to gain access to sensitive data, such as user credentials or financial information. SQL injection vulnerabilities occur when user input is not properly sanitized, allowing an attacker to inject malicious code into the database. For example, an attacker may enter a username like "Robert'); DROP TABLE Students; --" into a login form, which could potentially delete the entire "Students" table from the database. To prevent SQL injection attacks, developers should use prepared statements and parameterized queries, and ensure that all user input is properly sanitized.
Cross-Site Scripting (XSS) Vulnerabilities
Cross-site scripting (XSS) is a type of attack where an attacker injects malicious code into a web page, which is then executed by the user's browser. This type of attack can allow an attacker to steal user credentials, hijack user sessions, or take control of a user's browser. XSS vulnerabilities occur when user input is not properly validated, allowing an attacker to inject malicious code into a web page. For example, an attacker may enter a comment like "" into a blog post, which could potentially execute a malicious script on the user's browser. To prevent XSS attacks, developers should validate all user input and ensure that any user-generated content is properly sanitized.
Cross-Site Request Forgery (CSRF) Vulnerabilities
Cross-site request forgery (CSRF) is a type of attack where an attacker tricks a user into performing an unintended action on a web application. This type of attack can allow an attacker to perform actions on behalf of a user, such as transferring funds or changing passwords. CSRF vulnerabilities occur when a web application does not properly validate requests, allowing an attacker to forge requests on behalf of a user. For example, an attacker may create a malicious website that sends a request to a user's bank to transfer funds, which could potentially trick the user into performing an unintended action. To prevent CSRF attacks, developers should implement anti-CSRF tokens and validate all requests to ensure they come from a legitimate source.
Authentication and Session Management Vulnerabilities
Authentication and session management are critical components of web application security. However, vulnerabilities in these areas can allow an attacker to gain unauthorized access to a web application. Authentication vulnerabilities occur when a web application does not properly validate user credentials, allowing an attacker to gain access to sensitive data. Session management vulnerabilities occur when a web application does not properly manage user sessions, allowing an attacker to hijack a user's session. For example, an attacker may use a brute-force attack to guess a user's password, or exploit a session fixation vulnerability to hijack a user's session. To prevent authentication and session management vulnerabilities, developers should implement strong password policies, use secure password storage, and properly manage user sessions.
Input Validation and Sanitization Vulnerabilities
Input validation and sanitization are critical components of web application security. However, vulnerabilities in these areas can allow an attacker to inject malicious code into a web application. Input validation vulnerabilities occur when a web application does not properly validate user input, allowing an attacker to inject malicious code. Sanitization vulnerabilities occur when a web application does not properly sanitize user input, allowing an attacker to inject malicious code. For example, an attacker may enter a filename like "../etc/passwd" into a file upload form, which could potentially allow them to access sensitive system files. To prevent input validation and sanitization vulnerabilities, developers should validate all user input and ensure that any user-generated content is properly sanitized.
Conclusion
In conclusion, common vulnerabilities in web application security protocols can have serious consequences for online businesses and organizations. SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), authentication and session management, and input validation and sanitization vulnerabilities can all be exploited by attackers to gain unauthorized access to sensitive data. To prevent these types of attacks, developers should implement secure coding practices, validate all user input, and properly manage user sessions. Additionally, web application security protocols should be regularly tested and updated to ensure they remain effective against emerging threats. By prioritizing web application security, online businesses and organizations can protect themselves and their users from the ever-evolving threat landscape.

Post a Comment