Introduction to Secure Multiparty Computation
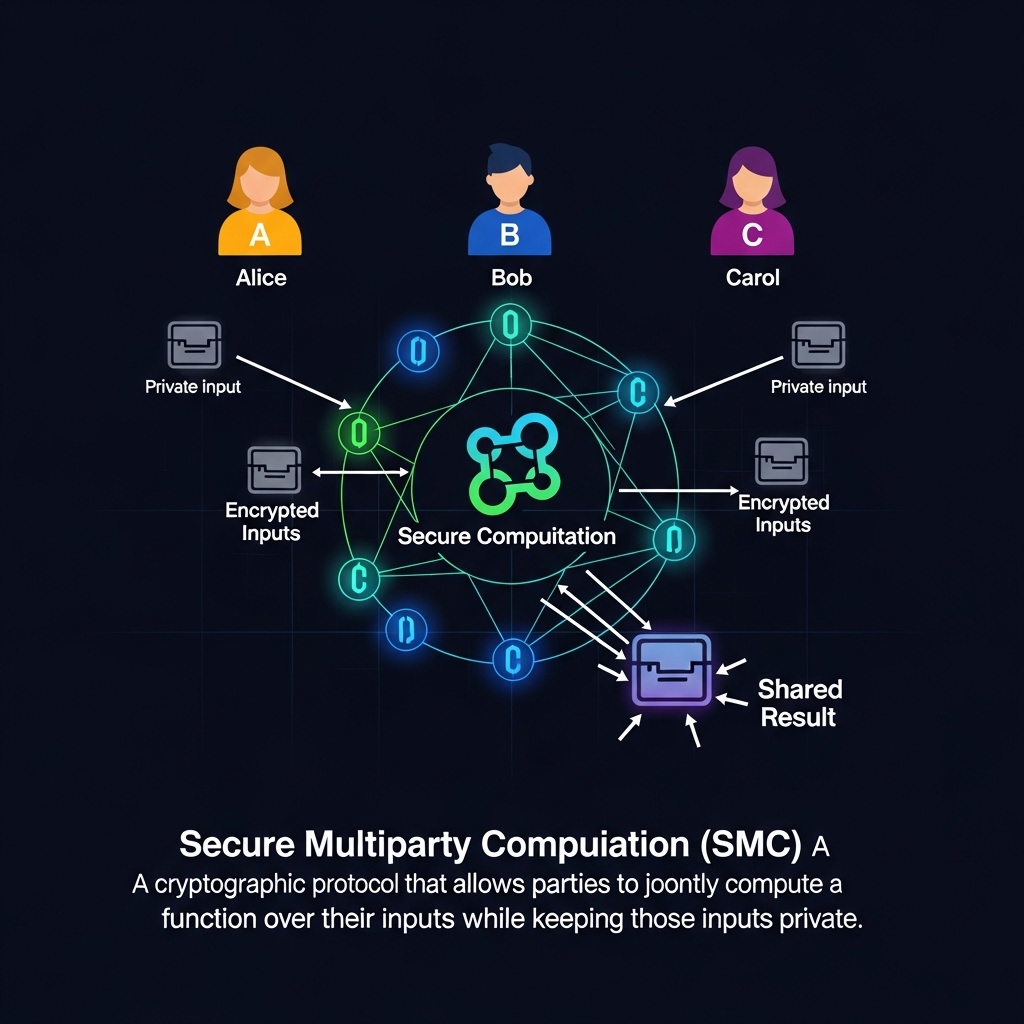
Secure multiparty computation (SMC) is a subfield of cryptography that enables multiple parties to jointly perform computations on their private data without revealing their individual inputs. This technique allows parties to collaborate on computations while maintaining the confidentiality and integrity of their data. SMC has numerous applications in various fields, including finance, healthcare, and social networks, where data privacy and security are of utmost importance. In this article, we will delve into the concept of secure multiparty computation, its importance, and its applications.
What is Secure Multiparty Computation?
Secure multiparty computation is a cryptographic protocol that enables multiple parties to perform computations on private data without revealing their individual inputs. In a typical SMC scenario, each party has a private input, and they want to compute a function of these inputs without revealing their individual data. The goal of SMC is to enable the parties to compute the desired function while maintaining the confidentiality and integrity of their data. This is achieved through the use of cryptographic techniques, such as encryption and secure protocols, to protect the data during the computation.
Importance of Secure Multiparty Computation
Secure multiparty computation is essential in various scenarios where multiple parties need to collaborate on computations while maintaining the confidentiality and integrity of their data. For instance, in the financial sector, SMC can be used to perform secure auctions, where multiple bidders submit their bids without revealing their individual bids. In healthcare, SMC can be used to perform statistical analysis on patient data without compromising patient confidentiality. Similarly, in social networks, SMC can be used to perform privacy-preserving friend suggestion algorithms.
Types of Secure Multiparty Computation
There are several types of secure multiparty computation protocols, including: 1. **Garbled Circuit Protocol**: This protocol involves creating a garbled circuit that represents the computation to be performed. Each party creates a garbled version of their input and sends it to the other parties. The parties then evaluate the garbled circuit to obtain the output. 2. **Homomorphic Encryption Protocol**: This protocol involves using homomorphic encryption to enable computations on encrypted data. Each party encrypts their input using a homomorphic encryption scheme and sends it to the other parties. The parties then perform computations on the encrypted data to obtain the output. 3. **Secret Sharing Protocol**: This protocol involves dividing each party's input into shares and distributing them among the parties. The parties then perform computations on the shares to obtain the output.
Applications of Secure Multiparty Computation
Secure multiparty computation has numerous applications in various fields, including: 1. **Secure Auctions**: SMC can be used to perform secure auctions, where multiple bidders submit their bids without revealing their individual bids. 2. **Privacy-Preserving Data Mining**: SMC can be used to perform privacy-preserving data mining, where multiple parties collaborate on data mining tasks without revealing their individual data. 3. **Secure Statistical Analysis**: SMC can be used to perform secure statistical analysis, where multiple parties collaborate on statistical analysis tasks without revealing their individual data. 4. **Privacy-Preserving Friend Suggestion**: SMC can be used to perform privacy-preserving friend suggestion algorithms, where multiple parties collaborate on friend suggestion tasks without revealing their individual data.
Challenges and Limitations of Secure Multiparty Computation
Despite the numerous applications of secure multiparty computation, there are several challenges and limitations associated with its implementation. These include: 1. **Scalability**: SMC protocols can be computationally expensive and may not scale well to large numbers of parties. 2. **Communication Complexity**: SMC protocols often require multiple rounds of communication between parties, which can be time-consuming and expensive. 3. **Security**: SMC protocols must be designed to ensure the confidentiality and integrity of the data, which can be a challenging task.
Conclusion
In conclusion, secure multiparty computation is a powerful cryptographic technique that enables multiple parties to jointly perform computations on their private data without revealing their individual inputs. SMC has numerous applications in various fields, including finance, healthcare, and social networks. However, its implementation is associated with several challenges and limitations, including scalability, communication complexity, and security. Further research is needed to address these challenges and make SMC more practical and widely applicable.

Post a Comment